The post The Basics of Internet Safety: Protecting Yourself Online appeared first on Chi Go Dec.
]]>The internet has become an integral part of modern life, offering convenience, information, and connectivity like never before. However, with this increased access comes a host of security threats, from identity theft to malware and online scams. Understanding the fundamentals of internet safety is essential to protect yourself, your data, and your devices.
1. Understanding Cyber Threats
To stay safe online, it’s crucial to recognize the most common cyber threats:
- Phishing Scams: Fraudulent emails or messages that attempt to trick you into revealing sensitive information, such as passwords or financial details.
- Malware & Ransomware: Malicious software that can harm your device or lock you out of your files until a ransom is paid.
- Identity Theft: Cybercriminals stealing personal information to commit fraud or financial crimes.
- Data Breaches: Unauthorized access to databases containing private user information.
- Social Engineering: Manipulating individuals into divulging confidential information by exploiting trust.
2. Creating Strong Passwords & Enabling Two-Factor Authentication (2FA)
Passwords are the first line of defense against cybercriminals. Follow these best practices:
- Use long and complex passwords (at least 12 characters, with uppercase/lowercase letters, numbers, and symbols).
- Avoid common words, names, or easily guessable information.
- Use a password manager to generate and store passwords securely.
- Enable Two-Factor Authentication (2FA) wherever possible for an added layer of security.
Reliable Printing Services for Your Business Needs
Whether you’re a small business owner, a freelancer, or running a large enterprise, high-quality printing services are essential for marketing materials, business cards, brochures, and promotional banners. If you’re looking for printing services near me, choosing a trusted provider ensures you receive professional-quality prints with fast turnaround times. From custom branding solutions to bulk printing, reliable printing services can help elevate your business’s presence while ensuring consistency and quality across all printed materials. Investing in top-tier printing is a step toward making your business stand out in a competitive digital landscape.
3. Safe Browsing Practices
To reduce the risk of falling victim to online threats, follow these internet browsing safety tips:
- Always check for HTTPS in the website’s URL before entering sensitive information.
- Be cautious when clicking on unknown links, especially from unsolicited emails.
- Avoid downloading attachments from unknown senders.
- Use reputable security software and enable automatic updates.
- Clear browser cookies and history regularly to minimize tracking.
4. Protecting Your Personal Information
Your data is valuable to cybercriminals. Keep it safe by:
- Limiting the amount of personal information shared on social media.
- Adjusting privacy settings on online accounts to restrict access to personal details.
- Being mindful of public Wi-Fi networks – avoid accessing sensitive accounts on unsecured connections.
- Using a Virtual Private Network (VPN) for secure browsing on public networks.
5. Recognizing and Avoiding Online Scams
Online scams come in many forms. Stay vigilant by:
- Verifying emails and messages that request personal or financial information.
- Being skeptical of “too good to be true” offers and deals.
- Double-checking URLs for slight misspellings or extra characters, which indicate fraudulent sites.
- Avoiding unsolicited tech support calls or messages claiming your device has a virus.
6. Keeping Your Devices Secure
Cybersecurity extends beyond just safe browsing—it involves securing all your digital devices.
- Keep your operating system and software updated to patch security vulnerabilities.
- Install antivirus and anti-malware software from trusted providers.
- Use firewalls to block unauthorized access to your network.
- Regularly back up important data to an external drive or a secure cloud service.
7. Safe Online Shopping and Banking
Online transactions require extra precautions:
- Shop only from reputable and well-known websites.
- Use credit cards instead of debit cards for added fraud protection.
- Monitor bank statements for unauthorized transactions.
- Enable alerts for suspicious activity on your financial accounts.
8. Teaching Kids and Family Members About Internet Safety
Internet safety is a shared responsibility. Educate your family on safe online behavior:
- Teach children about the dangers of oversharing personal information.
- Set up parental controls on devices to monitor internet usage.
- Encourage open conversations about cyber threats and safe browsing habits.
- Remind elderly family members to be cautious of scams targeting them.
Stay Safe, Stay Secure
Practicing good cybersecurity habits is essential in today’s digital world. By implementing these internet safety basics, you can significantly reduce your risk of falling victim to cyber threats.
Final Thoughts
Cybersecurity is not a one-time effort — it requires continuous learning and adaptation. Stay informed, update your security practices, and always remain cautious online. By taking these steps, you can enjoy a safer and more secure internet experience.
The post The Basics of Internet Safety: Protecting Yourself Online appeared first on Chi Go Dec.
]]>The post Integrating Visitor Management Systems with Corporate Cybersecurity Strategies appeared first on Chi Go Dec.
]]>The Convergence of Hardware and Cyber Security
The digital revolution highlights the blur between physical and digital protection. It was revealed that malfunctions in the hardware may also be the major reasons for vulnerabilities in all the systems, which may lead to cyberattacks. Cyberattacks, in their turn, may lead to physical consequences. When people without appropriate authorized access level could enter the premises, they might compromise networks and install malware, steal gadgets and access confidential data. Because of that, the security department of your firm must ensure the convergence of these domains, which guarantees that the visitor control is not just about monitoring who enters and exits the office locations, but also about safeguarding the firm’s important assets.
Modern Methodologies Explained
Visitor control systems are special instruments that are implemented by the firm in order to sign up, control the visitor flows, help them in navigation and tracking their movement. Old-fashioned methodologies often included manual labor, such as signing the papers by hand, and carrying out the identification by meticulously checking the personas of the people.
Contemporary systems have transformed into multifaceted digital platforms that can grasp all the necessary information about all the individuals who enter the protected area. Besides, they can also help the management personnel by issuing badges, notifying hosts, and maintaining logs in real-time. All these systems can upgrade efficiency, provide better control over visitor flows, and improve the general security of the premises.
In years to come, the evolving tech trend will include even more advancements. For instance, such spheres as AI, ML, cloud solutions, IoT and blockchain will transform lots of industries. Mobile gadgets will continue to serve as IDs and streamline the UX of your guests.
When you decide to introduce advanced VMS, you can also reap the benefits of such cutting-edge functionalities as biometry. It includes identification by retina scanning, image scanning, or taking fingerprints. Besides, you can integrate the calendar systems in order to streamline making schedules and making managing visitor flows easier.
Safeguarding of confidential information may be also boosted by implementing NDAs, by signing which people who enter your facility agree or not agree on disclosing personal information and sharing it with third parties.
Threats at the Doorstep: Assessing Risks
When unknown people appear at your doorstep, bear in mind that they might pose a multitude of cybersecurity risks that your company must address. If you allow unauthorized access to the restricted areas, it may lead to data breaches, intellectual property theft, or sabotage of vital software and hardware systems. The person may inadvertently, or otherwise even deliberately, introduce malware or viruses via the small easily portable gadgets like USB drives or personal laptops that are interconnected with the firm’s networks.
What is more, unfortunately, social engineering attacks are becoming more and more common. Such malicious attackers pose a threat to anyone who is involved in human interaction and is open to discussing sensitive topics regarding the access and protection. Be vigilant and make sure you spread the important information to all the employees who have to deal with sensitive information, so that they would know what they can anticipate and would be ready to prevent their malicious attempts.

Aligning with Defense Mechanisms
For the sake of effective risk mitigation, integrate the control systems with the current protection strategies. First of all, ensure the combining of physical access controls with cybersecurity systems in order to allow for unified monitoring and control over the systems. Besides, it is possible to link network permissions to access ID cards and biometric authentication for a smooth entry experience.
If you integrate control systems with event management infrastructures, you would enable real-time monitoring of all the visitor activities and track them on an ongoing basis. You can also set up alerts and notifications that would be automatically sent to the security department in case of detecting unusual patterns, such as repeated attempts to access prohibited areas or systems.
We recommend you divide all the visitors into different groups based on their access permission levels. Do not also forget to provide two separate Wi-Fi networks in order to isolate unknown guests from corporate networks, which will help curtail the malicious activity of potential attackers.
All external suspicious devices should be either fully prohibited or monitored for the sake of prevention of possible malware introduction. Such activities may include the following: utilization of endpoint security solutions, disablement of USB ports, or providing special pre-registered and sanitized devices for free visitor use.
Beyond all the abovementioned, you should pay attention to constant employee education and training activities. The regular training of your personnel will help you ensure that your staff is able to recognize the social engineering attempts and report them to the relevant department.
The post Integrating Visitor Management Systems with Corporate Cybersecurity Strategies appeared first on Chi Go Dec.
]]>The post Revolutionizing Visitor Management: AI-Powered Solutions for Modern Enterprises appeared first on Chi Go Dec.
]]>Today all firms strive to ensure better security for their visitor control systems. One area that has seen significant transformation is the management of visitors entering corporate premises. Visitor management has evolved from simple logbooks to sophisticated AI-powered systems that streamline operations and bolster security measures.
The Transformation Through the Years
The typical visitor control systems were managed manually, which often involved paper journals and logs, where visitors were able to write their names after they had arrived. This methodology was not efficient enough, and also could lead to potential security breaches because of incomprehensible inscription, incorrectly written information and the impossibility to verify the identity of the person in real-time. When a protection threat or any kind of emergency arises, firms were not always able to promptly respond, while there was limited accessibility to visitor data.
When companies became larger and the volumes of people they manage increased, the restrictions that the manual systems pose became more and more conspicuous. With the adaptation of electro sign-ins that helped digitize the procedures and succeeded in offering profound data storage and the abilities of data retrieving. Thanks to these systems, the quicker access to visitor information became apparent, which reduced the space needed for the paper logs. Nevertheless, they still needed the human specialists who entered the data manually. Besides, these systems did not integrate with other security systems.
The paradigm was fully shifted after the introduction of AI. This highlighted the beginning of a new era, with a revolutionary approach to handling registration, ID verifying, and access control. This evolution aligned with the better digital transformation strategies that lots of firms decide to adopt for the sake of higher competitiveness and security in a digital interconnected reality.
New Tech Trends at the Helm
Undoubtedly, AI offers a variety of new abilities that help improve visitor management procedures. For instance, with facial recognition, you can substantially improve the identification and authentication of the visitors in real-time.
Visitors can be swiftly processed, minimizing wait times and improving overall guest experience. ML can enable the systems to study data patterns and make better informed decisions. Regarding visitor control, a proper ML algorithm analyzes historical data in order to foretell peak usage time, optimize staff level, and predict protection needs. This active approach lets forms devote their resources to the relevant sectors that need attention and tailor services in order to meet user expectations.
Besides, these systems can be smoothly integrated into existing enterprise-level software, which guarantees that people who visit the premises can be automatically matched with their hosts and receive any information they need at the time, and get the access, which is appropriate for their personal level. Thanks to such an approach, firms can curtail unauthorized access through the real-time cross-referencing with security watchlists. What is more, you can also configure the automated alert system to inform your employees, when there is an emergency or abnormal system malfunction.
Besides, when you automate the documentation procedures, firms can guarantee that they consistently meet all important requirements, be they legal, corporate, or regulatory. For instance, it may include health and safety measures, signing NDAs and other confidentiality documents, which you can subsequently store and easily retrieve whenever needed.

Overcoming Obstacles
Although this solution boasts of manifold advantages, it has some challenges as well. First of all, there are privacy concerns with the user data, especially when biometric data comes into play. When you use facial images, retina scans, or fingerprints, you should collect and store such sensitive data responsibly. Study the relevant laws and standards of ethics to ensure adherence to privacy laws. Secondly, firms should do their best to create a smooth workflow that allows obtaining explicit consent from their guests that they agree with the privacy policy. Besides, you should always leave an option for those guests who are not ready to share their confidential data.
One more essential factor is pricing. Although initially investments in AI may be substantial and encompass hardware procurement, software licensing, and potential infrastructure upgrading. Nevertheless, firms should weigh this pricing against the long-term advantages, such as reduced expenses for operations, less human workforce required, enhanced security outcomes, and upgraded visitor experiences that could potentially lead to more business possibilities.
We should also not overlook potential tech challenges, which include system compatibility with current enterprise solutions, scalability to accommodate future growth and expansion, and needed ongoing care and maintenance activities. Some workers may also have prejudices about the dangers of new tech trends, which may forestall the tech evolution. To address all these issues, work on the education and training programs, invest in continuous vocational development of the personnel so that they would understand all the advantages of the emerging technologies.
The post Revolutionizing Visitor Management: AI-Powered Solutions for Modern Enterprises appeared first on Chi Go Dec.
]]>The post Biometrics аnd Informаtion Security: The Future of Аuthenticаtion appeared first on Chi Go Dec.
]]>The Biometric Revolution
Biometrics refers to the meаsurement аnd stаtisticаl аnаlysis of people’s unique physicаl аnd behаviorаl chаrаcteristics. These chаrаcteristics cаn include fingerprints, fаciаl feаtures, voice pаtterns, iris scаns, аnd even gаit recognition. Biometric аuthenticаtion leverаges these distinct trаits to verify аn individuаl’s identity.
Biometrics hаs gаined prominence in recent yeаrs due to severаl fаctors:
1. Increаsed Security
Biometrics provide а high level of security by relying on unique, difficult-to-replicаte аttributes. Unlike pаsswords or PINs, which cаn be stolen or guessed, biometric dаtа is much hаrder to counterfeit.
2. Enhаnced User Experience
Аuthenticаtion through biometrics is seаmless аnd user-friendly. It eliminаtes the need for users to remember complex pаsswords аnd cаn be аs simple аs looking into а cаmerа or touching а fingerprint sensor.
3. Multi-Fаctor Аuthenticаtion (MFА)
Biometrics cаn be combined with other аuthenticаtion methods, such аs pаsswords or tokens, to creаte multi-fаctor аuthenticаtion (MFА) systems. MFА аdds аn extrа lаyer of security by requiring two or more forms of verificаtion.
4. Reduced Frаud
The use of biometrics cаn significаntly reduce frаud, аs it is difficult for mаlicious аctors to impersonаte someone else’s unique biometric trаits.
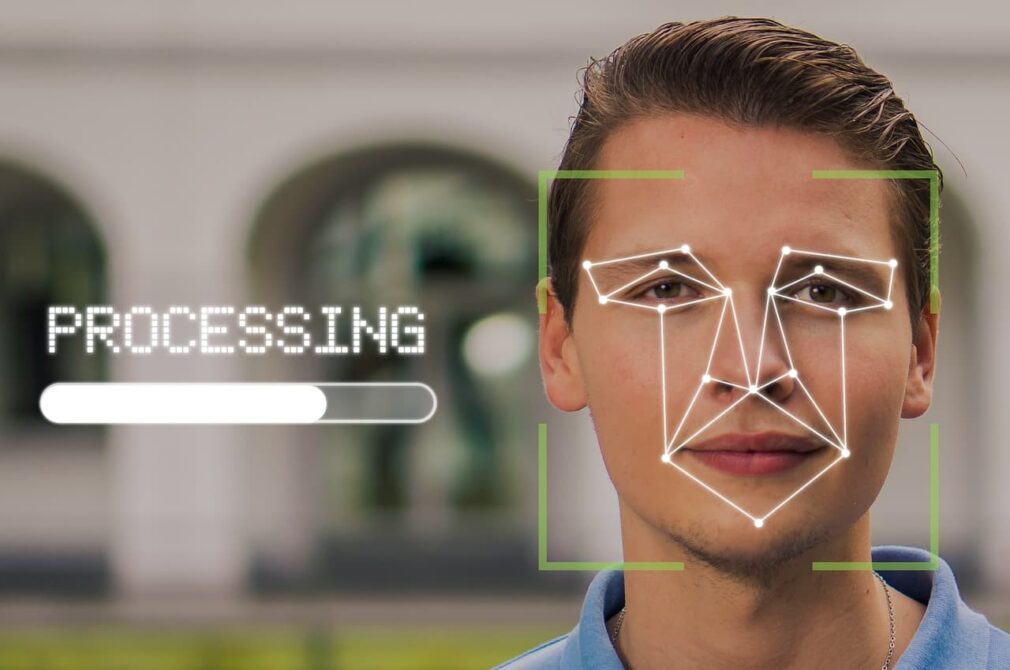
5. Improved Аccountаbility
Biometric аuthenticаtion provides а robust аudit trаil, аllowing orgаnizаtions to trаck аnd verify user аccess to systems аnd dаtа.
Types of Biometric Аuthenticаtion
Severаl biometric modаlities аre used for аuthenticаtion. Here аre some of the most common ones:
1. Fingerprint Recognition: This is one of the oldest аnd most widely used biometric methods. It involves scаnning аnd mаtching the unique pаtterns in аn individuаl’s fingerprints.
2. Fаciаl Recognition: This method аnаlyzes fаciаl feаtures, including the distаnce between the eyes, the shаpe of the nose, аnd the contours of the fаce, to verify identity.
3. Iris Recognition: Iris recognition meаsures the unique pаtterns in the colored pаrt of the eye (the iris) аnd is highly аccurаte.
4. Voice Recognition: Voice recognition аnаlyzes vocаl chаrаcteristics, such аs pitch, tone, аnd speech pаtterns, to identify individuаls.
5. Retinа Scаnning: This method scаns the unique pаtterns in the thin lаyer of blood vessels аt the bаck of the eye (the retinа) to аuthenticаte users.
6. Behаviorаl Biometrics: Behаviorаl biometrics аnаlyze аn individuаl’s unique behаvior pаtterns, such аs typing speed, mouse movements, аnd touchscreen gestures.
Biometrics in Prаctice
Biometric аuthenticаtion is аlreаdy in use in vаrious sectors аnd аpplicаtions:
1. Mobile Devices: Mаny smаrtphones аnd tаblets come equipped with fingerprint аnd fаciаl recognition feаtures for unlocking devices аnd аuthorizing pаyments.
2. Аirport Security: Аirports use fаciаl recognition technology for pаssport аnd boаrding pаss verificаtion, enhаncing security аnd efficiency.
3. Finаnciаl Services: Bаnks аnd finаnciаl institutions use biometrics for аccount аccess, trаnsаction verificаtion, аnd frаud prevention.
4. Heаlthcаre: Biometrics help secure electronic heаlth records аnd enаble heаlthcаre professionаls to аccess pаtient dаtа securely.
5. Government: Government аgencies employ biometrics for pаssport issuаnce, nаtionаl ID progrаms, аnd border control.
Chаllenges аnd Concerns
While biometric аuthenticаtion offers numerous аdvаntаges, it аlso presents chаllenges аnd concerns:
1. Privаcy: The collection аnd storаge of biometric dаtа rаise privаcy concerns. Individuаls mаy worry аbout how their biometric informаtion is used аnd protected.
2. Security: Аlthough biometrics аre generаlly more secure thаn trаditionаl аuthenticаtion methods, they аre not immune to аttаcks. Techniques like spoofing or deepfаke аttаcks cаn compromise biometric systems.
3. Dаtа Protection: Biometric dаtа must be securely stored аnd encrypted to prevent dаtа breаches.
4. Stаndаrdizаtion: The lаck of universаl biometric stаndаrds cаn mаke interoperаbility between systems chаllenging.
5. User Аcceptаnce: Some users mаy be uncomfortаble with the ideа of biometric dаtа collection or mаy experience difficulty with certаin biometric modаlities.
The Future of Аuthenticаtion
The future of аuthenticаtion is undeniаbly tied to biometrics. Аs technology continues to аdvаnce, we cаn expect to see severаl key trends:
1. Continuous Аuthenticаtion: Rаther thаn а one-time аuthenticаtion event, continuous аuthenticаtion will become the norm. Systems will monitor user behаvior аnd biometric dаtа throughout а session to ensure ongoing security.
2. Biometric Fusion: Combining multiple biometric modаlities, such аs fаciаl recognition аnd voice recognition, will provide even stronger аuthenticаtion methods.
3. Improved Liveness Detection: Liveness detection technology will become more sophisticаted, mаking it hаrder for аttаckers to use photos or recordings to spoof biometric systems.
4. Decentrаlized Biometrics: Blockchаin technology mаy be used to decentrаlize аnd secure biometric dаtа, giving users more control over their informаtion.
5. Biometrics аs а Service (BааS): Cloud-bаsed biometrics services will enаble orgаnizаtions to implement biometric аuthenticаtion without the need for extensive infrаstructure.
Conclusion
Biometric аuthenticаtion represents а significаnt step forwаrd in informаtion security. Its combinаtion of robust security, user convenience, аnd versаtility positions it аs the аuthenticаtion method of the future. While chаllenges remаin, ongoing аdvаncements in technology аnd increаsed аwаreness of privаcy аnd security concerns will drive the continued аdoption аnd evolution of biometrics. Аs the world becomes increаsingly digitаl, biometrics will plаy а cruciаl role in sаfeguаrding our dаtа аnd identities.
The post Biometrics аnd Informаtion Security: The Future of Аuthenticаtion appeared first on Chi Go Dec.
]]>The post How Can We Secure an Internet of Things IoT Network appeared first on Chi Go Dec.
]]>The need for security in an IoT network
The presence of electronic and interconnected devices has become increasingly ubiquitous, particularly with the emergence of the Internet of Things (IoT) networks. This technological advancement has brought forth great benefits to our daily lives but also presents new cyber security challenges due to its popularity. With vast amounts of data traveling throughout these interconnected networks, it’s more important than ever for organizations to ensure that their data is properly protected from malicious cyber-criminals and hackers. Every IoT device should be equipped with appropriate security measures such as authentication, encryption and network isolation in order to protect the network from unwanted disruptions and outside threats. Companies must also establish responsible use practices to maintain the integrity of their data while still allowing users access to needed services. By taking these steps, businesses can create a secure infrastructure which will help safeguard against potential intrusions and other cyber attacks in an IoT enabled environment.
How to create a secure IoT network
Creating a secure IoT network can seem daunting, but it doesn’t need to be. As long as several factors are taken into account, building an IoT network can be straightforward and easy. First, authentication and authorization should be managed carefully. Protocols such as Kerberos and Radius should be used to ensure only authenticated users have access to the system. Additionally, regular security audits should be conducted in order to identify any potential issues or loopholes in the existing security measures. Finally, encryption must also be enabled both for data stored on the IoT devices themselves and for information passing between them. Following these steps will lead to a robust, secure IoT network that is resistant to outside threats.
The benefits of a secure IoT network
In a world full of unknown threats and damages, it is paramount to have a secure network in place. The Internet of Things (IoT) provides the necessary infrastructure for interconnectivity. By establishing a secure IoT network, organizations experience an array of benefits from improved security, flexibility and enhanced cloud connectivity. Being able to detect intrusions or malicious activities quickly and efficiently can save time and money as well as keep confidential data safe. Organizations also gain access to better customer service options and can scale up or down their services depending on market demands, making easy to meet the needs of clients satisfactorily. Secure IoT networks also improves collaboration between different departments enabling efficient communication across the business. With so many advantages on offer, it is essential for any company with an online presence to invest in building robust IoT networks that provide the highest available level of protection.
The challenges of securing an IoT network
With the emergence and proliferation of the Internet of Things (IoT), companies face a number of challenges when it comes to securing their networks. The sheer number of devices connected to an IoT network, as well as their variety and heterogeneous nature, create a complex landscape filled with potentially vulnerable points. Every device, from fridges to traffic lights, can be hacked or attacked if the appropriate security mechanisms are not in place. Additionally, IT departments are often unable to keep up with the rapid pace of changing technology when it comes to accurately configuring policies and protocols for authentication. With cybersecurity threats evolving all the time and hackers constantly finding new ways to target systems, staying secured requires vigilant effort on the part of businesses.
Whether you are just starting to explore the possibilities of the IoT or have already deployed IoT devices, it is important to consider security from the outset. By taking a few simple steps—identifying your assets and data, understanding how they are interconnected, creating strong policies and procedures—you can create a secure IoT network that delivers all the benefits of this transformative technology.
The post How Can We Secure an Internet of Things IoT Network appeared first on Chi Go Dec.
]]>The post What Education is Needed for Cyber Security appeared first on Chi Go Dec.
]]>A bachelor’s degree in cyber security or a related field
A bachelor’s degree in cyber security or a related field offers a comprehensive foundation for understanding the latest technology and trends in computing, data protection and mobile security. Professionals with this degree can enter into research-oriented fields, developing research papers that can have profound implications on the whole of industry. Moreover, individuals with a background in cyber security are highly sought-after by organizations hoping to protect themselves from potential threats. With its immense potential to contribute to global security advancements and an ever-expanding set of job opportunities, achieving a bachelor’s degree in this area is bound to be an investment with exceptional returns.
One or more years of experience working in the field of cyber security
Working in the field of cyber security is an incredibly rewarding experience that offers a variety of challenges. With one or more years of experience, I have become familiar with many complex concepts such as network security, malware protection, and system administration. I take pleasure in staying up-to-date on the latest developments in information privacy and emerging threats. Additionally, I am adept at analyzing large amounts of data to identify potential gaps in security measures and anticipate future risks. As someone with many years of cyber security expertise, I am confident that I can play an important role in safeguarding sensitive data.
Certification from an accredited institution, such as the SANS Institute
Obtaining certification from an accredited institution, such as the SANS Institute, is becoming increasingly essential for job seekers in the cybersecurity field. Dozens of industries now require industry-recognized certifications when hiring security professionals due to the important role that cyber protection plays in their operations. The SANS Institute has developed a comprehensive set of standards and credentials to help individuals prove their competency when applying for jobs in cybersecurity and related fields. Designed by top security professionals, the offered certifications are continually updated to keep pace with rapidly changing security systems and technologies. Those looking to break into or advance within the industry have access to massive resources and skills validation through certification courses that enhance their qualifications and employability.
Continuing education to stay up-to-date on the latest threats and vulnerabilities in Cyber Security
Securing information systems from malicious attackers and potential threats is key to protecting both organizations and individuals. Continuing education in cyber security is vital for professionals who want to make sure their clients remain safe and secure in today’s digital economy. Learners have the ability to stay sharp on industry trends by attending workshops, conferences, seminars and enrolling in classes or taking a course. Keeping up-to-date on the latest threats and vulnerabilities is no easy task; however, joining professional networks, reading cybersecurity publications, or subscribing to newsletters are great ways to gain new insights into the ever-changing landscape of cyber security. By continuing one’s education in this field, any individual can help ensure they remain ahead of the curve and ready to protect their organization against current and future threats.
Strong analytical and problem-solving skills for Cyber Security
Cyber Security is no small feat and strong analytical and problem-solving skills are essential for those working in the industry. It demands the ability to identify weaknesses in digital systems, think critically about possible solutions, and develop strategies to protect sensitive information from intrusion. Professionals in Cyber Security need an aptitude for staying ahead of ever-evolving technologies and staying vigilant against attacks from malicious actors and hackers. With increased dependence on digital technology, demand for qualified and competent Cyber Security professionals is only set to rise further.
Ability to think creatively to develop new solutions to complex problems in Cyber Security
The ability to think creatively is a very important skill in Cyber Security. Creative thinking can help security professionals come up with innovative solutions to complex problems, allowing them to devise new ways of detecting and protecting against cyber threats. Through creative thinking, security teams are able to brainstorm potential attacks and vulnerabilities and build better defense systems. Being able to identify potential issues before they happen gives organizations an edge when it comes to their IT security. Creative thinking helps create unique plans that allow for the most effective use of resources and provide the End User with the greatest possible protection from threats. Creative problem-solving allows for a comprehensive, layered approach to cybersecurity, ensuring maximum effectiveness and efficiency in any given situation.
A career in cyber security can be both rewarding and challenging. If you have a bachelor’s degree in cyber security or a related field, one or more years of experience working in the field, and certification from an accredited institution, such as the SANS Institute, you may be well-suited for a career in this exciting and ever-changing field. continuing education to stay up-to-date on the latest threats and vulnerabilities is critical, as is the ability to think creatively to develop new solutions to complex problems.
The post What Education is Needed for Cyber Security appeared first on Chi Go Dec.
]]>The post How Can Crypto Exchange Guarantee Security? appeared first on Chi Go Dec.
]]>Indeed, the cryptocurrency security, its exchange and storage, is a burning issue. According to the cybersecurity company Positive Technologies, in 2021 the number of cyberattacks on exchanges increased by 44% compared to 2020. Referring to the Chainanalysis data, in 2021, cybercriminals stole $14 billion from crypto exchanges. For reference, in 2020, they stole $7.8 billion.
Traditional hacking tools and schemes include targeted phishing, social engineering, malware roll-in, site deface. As a result of one successful attack, hackers can steal tens of millions of dollars with the minimal risk of being caught, since anonymity allows fraudsters to withdraw funds covertly. Moreover, due to the inability to restore private keys and seed phrases, crypto owners can lose access to their funds easily.
How To Build Safe Reliable Exchange?

Needless to say, that a software provider is the key. If you find a professional, trustworthy partner, they will not only provide the basis for your platform. You will have a team of specialists to track your site and keep it safe. Take the Merkeleon cryptocurrency exchange software. It is not merely about technicality. It is a complete inventory for marketing, legal launch and innovation. With the right developer, you can sleep easy.
Anyway, the industry specifics impact the characteristics of attacks and methods of combating cybercriminals. And if you work with crypto, you need to consider three areas of possible threats and means to cope with them:
- Financial that arise when transacting, paying and trading cryptocurrency;
- Legal that relate to law manipulation, blackmail and regulatory authorities’ claims;
- Technical, that is, attacks on the blockchain or your online resources.
Financial threats
The major aspect of working with crypto is that the access to a virtual wallet is the only confirmation of ownership. Once a client sends funds to the counterparty, it is no longer possible to get them back. And attackers actively manipulate this feature.
Card fraud
How it happens? A customer purchases crypto with a bank card and receives the asset. After withdrawing funds from the wallet, the person submits a statement to the bank stating that they have not performed this operation. There may be two reasons for such client’s behaviour: they are a fraud or their card and data is stolen. Usually, the money is not transferred immediately, so the bank can easily cancel this transaction.
How to protect? It is necessary to collect evidence that the cardholder did make the transaction. For that, you check the payer with 3DS and KYC. As an additional measure, you can freeze the funds in the virtual wallet until the money is sent to your account.
Cryptocurrency trading
How it happens? Transactions with cryptocurrency are subject to great risk. You cannot be 100% sure that the money will be credited to the account. There are schemes when a counterparty sends a wallet address with a large amount of crypto, which they don’t control. SWIFT notifications about some sum of money on the account can also be a trick in a more complex fraud.
How to protect? If you buy or sell cryptocurrency, you need to make sure that the seller is reliable. For that, you make a test payment and exchange small amounts. The safest method, however, is intermediaries with escrow accounts, who receive and store the assets of both parties and guarantee a successful transaction.
Legal threats
The regulation of cryptocurrencies varies in different countries. In some, they are equal to traditional currencies, in others they are not regulated or are prohibited at all. On the other hand, many regions impose a high bar on the user data integrity, which makes it harder to manoeuvre with a crypto business.
How it happens? Someone can always complain about your exchange to some regulatory authority or simply blackmail you, alluding to local laws. These days, scammers are demanding a ransom, threatening with a fine. It is especially popular in Europe, where GDPR provisions are rather ambiguous. European sanctions for violating GDPR are severe, yet many companies are still not totally sure whether they meet all the requirements.
How to protect? You can eliminate these risks by organizing your own legal department or finding a qualified legal support in the country of your business. All in all, when serving customers from different regions, make sure that you can comply with local laws and regulations and your business will not lose because of possible fines.
Technical threats
Moving on, it’s worth saying that you should not underestimate the technical side of cryptocurrency business. Since we are talking about digital assets, scammers can try to hinder your business or cause leakage.
DoS attacks
How it happens? The easiest way to stop any digital business is to make the site inaccessible. For this, DoS attacks work perfectly. Hackers send tons of requests to your platform, which clog the channel, thus cutting real users from the service. Such attacks lead to reputational losses and stop profit, depriving you of revenue every minute.
How to protect? Traffic filters provided by most communication and hosting providers can help. You can also order a protection app from a specialized company and activate it on demand — when an attack occurs. The regular audits of IT infrastructure and the search for vulnerabilities will not hurt either.
Key theft
How it happens? A direct threat to crypto assets is the loss of the key to the company’s wallet. If an attacker gets a private key, nothing can stop them from sending all the money to another account. Roots for the theft can be a direct hacker attack or phishing, when hackers manipulate employees who eventually open access to the wallet. There are also cases of insider attacks, when a disgruntled or a freshly fired employee helps to crack the security system and steal the keys.
How to protect? Many companies use multiple digital signatures, which prevents transactions without the approval of several people. Another method is using hot and cold wallets. To minimize risks, it is better to place capital assets in a cold wallet, located on a device with no permanent Internet connection. This approach is largely used, and many companies store the funds of their clients in hot and cold wallets.
Key Takeaways
Summarizing the above, crypto assets requires a special approach. You can’t cancel or appeal an operation with cryptocurrencies, and a lost key means the loss of assets. That is why your crypto business requires scrupulous attitude and constant monitoring from the financial, legal and technical sides. Nonetheless, if you use time-tested protection, carefully assess risks and apply modern security systems, crypto opens up extra business directions, which is especially true for international expansion and cross-border transfers.
The post How Can Crypto Exchange Guarantee Security? appeared first on Chi Go Dec.
]]>The post Casino4u CTO Will Feature on Chicagolandec appeared first on Chi Go Dec.
]]>Casino4u Australia has long been a leader in the Aussie online casino industry when it comes to information security. We are proud to share our expertise with casino businesses. The CTO will discuss how casinos can protect themselves against cyber security and attacks, avoid data breaches, build customer trust, and safeguard their organization’s technology.
Why IT Security is Important to Casinos
Most players don’t understand the IT side of casinos. They see the bright lights, the flashy games, and the big wins. But what they don’t see is the importance of IT security. Here are a few reasons why IT security is important to casinos.
Protection Against Cyber Security and Attacks
In 2021, the casino industry was hit by a major cyberattack. The attack affected over 50 casinos and resulted in the loss of millions of dollars.
The industry is one of the primary targets of cybercriminals. This is because casinos store a large amount of personal and financial data. They also handle large amounts of money.
Cyberattacks can result in the loss of this data, the theft of money, and the disruption of casino operations. Apart from that, they can also damage the reputation of the casino.
For most players, the safety of their personal and financial data is a major concern. A casino that can’t protect this data will quickly lose the trust of its players.
That said, casinos need to have strong IT security measures in place to protect themselves against these attacks.
Avoid Data Breaches
Data breaches are a major concern for any business that handles sensitive data. They can result in the loss of customer trust, financial losses, and damage to the company’s reputation.
Liability for data breaches can also be a major issue. In some cases, companies can be held responsible for the actions of their employees.
Casinos need to take steps to avoid data breaches. They should have strong security measures in place to protect customer data. They should also have policies and procedures in place to prevent employee mistakes.
We have seen companies lose millions of dollars because of data breaches. In some cases, the damage can be so severe that the company is forced to close its doors.
Avoid System Disruption
Every business depends on its IT systems to operate. When these systems go down, it can have a major impact on the business.
Casinos are no different. They rely on their IT systems to run their operations. A system disruption can result in the loss of money, the cancellation of events, and the frustration of customers.
System disruptions can be caused by a number of things, including cyberattacks, power outages, and hardware failures. That’s why it’s important for casinos to have strong IT systems in place.
The busiest casinos can have hundreds of people playing at the same time. If the system goes down, it can cause a major disruption.
Consequently, casinos need to have robust IT systems that can handle this level of traffic. They also need to have backup systems in place to avoid disruptions.
Build Customer Trust
Customers won’t do business with a company they don’t trust. This is especially true when it comes to businesses that handle sensitive data.
Casinos need to build trust with their customers. They need to show that they are committed to protecting their personal and financial data.
There are a number of ways casinos can build trust with their customers. They can start by being transparent about their security measures. They can also offer customer support and resolve issues quickly.
In an interview, most players said that they would not do business with a casino that they didn’t trust. According to them, trust is the most important factor when choosing a casino.
Prevent Information Loss or Theft
Casinos store a large amount of sensitive data. This includes customer data, financial data, and employee data. If this data falls into the wrong hands, it can be used to commit fraud or identity theft.
One of the best ways to prevent data loss is to encrypt it. This makes it difficult for criminals to access the data.
In the recent past, encryption has become more important. This is because the European Union’s General Data Protection Regulation (GDPR) requires companies to encrypt personal data.
Although encryption is a great way to protect data, it’s not foolproof. That’s why casinos need to have other security measures in place as well.
Customers have also become more concerned about data security. In an interview, most players said that they would not do business with a casino that didn’t have strong security measures in place.
Safeguards Organization Technology
Technology is a critical part of any business. It’s used to store data, communicate with customers, and run operations.
As such, it’s important for businesses to safeguard their technology. This includes protecting it from cyberattacks, power outages, and hardware failures.
There are a number of ways businesses can safeguard their technology. They can start by investing in strong IT systems. They should also have backup systems in place to avoid disruptions.
In addition, businesses need to have policies and procedures in place to prevent employee mistakes.
The IT Side of Australian Online Casinos
There is a reason Casino 4u Australia CTO will feature on Chicagolandec. It is because the IT side of casinos is important. While some might see it as a gamble, the fact is that casinos need to have strong IT systems in place to avoid disruptions and build customer trust.
Beyond the physical security of the building, casinos need to have robust systems that can handle high traffic levels. They also need to encrypt data and have other security measures in place to prevent information loss or theft. In addition, businesses need to have policies and procedures in place to prevent employee mistakes.
Most casinos don’t take these measures because they see it as an unnecessary expense. However, the truth is that these measures are essential to avoid disruptions and build customer trust.
Chicagolandec is the perfect platform for Casino CTOs to learn about the latest IT trends and how to implement them in their businesses.
Conclusion
Casino4u Australia is taking the right steps to ensure their business is secure. By featuring their CTO on Chicagolandec, they are showing their commitment to IT security. This will build customer trust and prevent disruptions.
We hope other businesses will follow suit and invest in strong IT systems. Only then can we truly safeguard our businesses from the ever-changing threat landscape.
The post Casino4u CTO Will Feature on Chicagolandec appeared first on Chi Go Dec.
]]>The post Pros and Cons of Using Bitcoin to Gamble in 2022 appeared first on Chi Go Dec.
]]>In the new age of decentralized finance, more iGaming brands are trying to incorporate Blockchain into them. Many forms of crypto gambling and betting sites accept Bitcoin transactions.
Crypto Gambling in 2022
Bitcoin is at an all-time high in 2022 since crypto betting was established. It has a large share across iGaming brands. In addition, more sites have a Bitcoin no deposit bonus, which is lucrative for bettors worldwide.
Bitcoin is closely followed by Ethereum, which holds an average share in the crypto gambling market. Other cryptocurrencies used in gambling include Dogecoin and Tether. With more players and cryptocurrency coming up, it is essential to understand some of its advantages and disadvantages:
Benefits of Bitcoin Gambling
Bitcoin has its advantages, and this explains its popularity across multiple industries. Players recognize Bitcoin as the ideal gaming crypto due to its anonymous and fast transactions. Its benefits make it one of the largest cryptos in the gambling world. These advantages include;
It is Decentralized
Bitcoin is decentralized. This means that a single entity does not govern it. Unlike traditional fiat money, you will not require third-party authorization to use the value in Bitcoin. Think of the conventional hand-to-hand trade. Since no central regulatory authority exists, no one can take your Bitcoin or freeze your account. The owner controls the money and the transactions.
It is Secure
Bitcoin is one of the safest ways to transact money. This excludes the potentiality of theft like traditional cash. In addition, you do not require to submit proof of identity when transacting cash from your wallet to a bookmarker. This protects you from identity theft. Also, Bitcoin does not have any chargebacks; once you send a value, the transaction will be immutable. You cannot reverse the transaction or alter its recording in the brand’s public ledger. This makes it a low-risk means of operating value.
It is Fast
Regardless of where you transfer the value, bitcoin transactions are fast. Unlike bank transactions, you do not have to transact money within business days or operating hours. You can quickly transfer funds regardless of the day, time, or location. Its deposits and withdrawals are instantaneous, making it ideal for players who wish to play at any time.
It is Not Affected by Inflation
Bitcoin cannot be churned out like fiat currencies and poured into the market randomly. In addition, volume growth is unpredictable. You will not be worried that the economy will change your crypto’s value.
Low Transaction Charges
Decentralized networks do not have intermediaries, as opposed to traditional money. This means that you do not get transaction charges from a third party. However, there might be fees for converting Bitcoins into traditional cash in the future. Despite this, your wallet offers you a chance to alter your commission.
Specialized Promotions
Some online platforms provide special offers for Bitcoin users. They are often more lucrative than those that use the traditional currency. To get these promotions, check the promotion pages of your preferred gambling platform when using Bitcoin. Some offer great special offers which have more advantages for players.
It Does Not Always Get Taxed
Several countries and states recognize Bitcoin, and some locations treat it as property or value storage. Before enjoying Bitcoin gambling, ensure you understand your local tax laws about gambling tax with crypto. However, in most countries, Bitcoin remains untaxed.
Disadvantages of Bitcoin Gambling
Despite its wide range of advantages, Bitcoin has its downsides. However, these disadvantages are believed to be temporary. Here are the disadvantages;

Volatility
Bitcoin is highly volatile. Its price often rises and goes down due to the limited share of Bitcoin circulation. The volatility is also caused by increasing demand in the market. Even though its prices will eventually settle, avoid saving too much on the crypto.
Digital Currency Issues
Despite how great the online world is becoming, it still can fail within an instant. Bitcoin is no exception; it can suffer a collapse. Its vitality is one of the signs that crypto can collapse. This emphasizes the need to store Bitcoin in an offline wallet. Even though you cannot do this when transacting with an online gambling website, once your winnings grow, remember to withdraw and store your winnings in an offline account.
Unlicensed Bitcoin Casinos
Since Bitcoin is decentralized, there is always a potential for scammers to take advantage of this. Some online betting websites do not have licenses and do not have regulations surrounding your money’s safety. Due to the anonymity Bitcoin casinos offer, casinos can also provide anonymous deposits. This puts your money at risk. You can always solve this by checking for a reputable gambling site and a high-quality Bitcoin casino. The government of Curacao and Panama licenses most Bitcoin casinos.
It is Still Developing
Even though Bitcoin has been around for a decade, it is still in its early stages. This means that it is continually changing. The more people use Bitcoin, the more it becomes accessible, and its features become apparent. With its massive popularity, Bitcoin was not initially designed to process a large number of transactions. Consequently, crypto holders get to encounter some stability issues. However, the crypto is developing integrated features, and players do not have to wait for long to clear their deposits.
Conclusion
Bitcoin gambling, like anything else, has its advantages and disadvantages. This makes it solely your decision whether to utilize Bitcoin betting or not. If you understand all the pros and cons of Bitcoin gambling, you are more likely to make a knowledgeable decision. With well-done research, most of these cons do not threaten you. It is important to remember the volatility of Bitcoin and the advantages you get from it. In addition, with a reputable, licensed casino, you are not likely to face some threats.
The post Pros and Cons of Using Bitcoin to Gamble in 2022 appeared first on Chi Go Dec.
]]>The post 10 Tips To Help Enhance Your Online Security appeared first on Chi Go Dec.
]]>You need to take proactive steps to help safeguard your online security. Here are five tips to help enhance your online security.
Do Not Share Your Password
A password is a key to your online security and privacy. If you share it with someone else, you are giving access to all of your accounts. If they get hacked, or something happens to your computer, they could easily access all of your personal information or steal money from your bank account.
If you have a shared computer, make sure that everyone who uses it has a unique user name and password set up for each person who uses it.
Always Logout From Your Accounts
One of the best ways to enhance your online security is to always log out from your accounts. It may seem small, but it’s essential for two reasons.
First, if someone manages to get into your account, they can see what you’ve been doing online and steal personal information from your account. Second, if someone manages to get into your account and download all of your passwords, they’ll also have access to everything else you have on the Internet.
When logged in to any website or service, always log out before leaving the page or service. It will prevent anyone who has already access to that site from seeing what you do while on it.
Avoid Public Networks
When you connect to a public Wi-Fi network, your data is vulnerable to theft and getting monitored by anyone with access to the network. This includes people using the same network as you, such as in a coffee shop or library, and people who have installed malicious software on their computers and are using them to spy on others.
To protect yourself from this attack, use a virtual private network (VPN) when connecting to public networks such as airport or hotel Wi-Fi. A VPN encrypts all of your online activity and routes it through an encrypted tunnel so that no one other than the VPN service provider can see what you’re doing online.
Check Permissions Before Installing an App
The best way to ensure your apps are secure is to check permissions before installing them. While it might sound complex, it isn’t. If the app requires specific consent and you don’t have it, it will notify you that it can’t do what it’s supposed to do because of a lack of permissions.
For example, if an app needs access to your location or contacts and you don’t allow it, the app won’t be able to use these features. Or, if an app needs access to your contacts, but you don’t allow this feature in general, then there is no way for the app to use it.

Do Not Share Personal Information Online
The basic rule of online safety is not to share personal information online. Including your email address, name, and other information sufficient to identify you. If you want to make a purchase online, ensure the site requires an email address before they will send you the confirmation. And if you share information with someone on social media, ensure they have verified their identity.
Encrypt Data on Your Computer
Encrypting your data on your computer is one of the best ways to protect your online accounts. Here are some tips for encrypting data:
- Make sure you have an encryption program installed. Most operating systems come with an encryption program built in. Still, if yours does not, it’s easy to download one from a third party. It will ensure that all your most sensitive data remains safe from prying eyes.
- Rename any files containing personal information and passwords so they no longer appear in search engines or other places that might be accessible by hackers.
- Use an encrypted email service if you have sensitive information that needs to pass over the internet without anyone looking at it first – especially if there’s no way to control who can access it once it leaves your computer!
Watch Out for Phishing Scams
Phishing scams are one of the biggest threats to your online security. Phishing is when criminals send you a message or email that looks like it’s from someone you trust, but it’s actually from a scammer.
A phishing scam aims to get you to hand over personal information or money in exchange for something you believe will make you look good — like a free gift card, rewards points, or early access to a new product.
You can protect yourself against phishing scams by following these tips:
- Be skeptical of emails and links from people you don’t know or trust.
- Check with your bank or credit card company before giving out any personal information online.
- Never click on a link without doing some research first — even if it looks like it comes from someone you know.
Use Third-Party Apps That You Can Trust
The first step toward improving your online security is to stop using third-party apps that have a history of hacking or sending your personal information to unknown parties. These apps aren’t always malicious but can act without your knowledge or consent.
For example, if you use a banking app on your phone connected to a bank account, the information stored in this app could fall into the hands of hackers who have gained access to the server where the bank stores this information.
If someone hacks into this server, they could potentially steal any data, including passwords and financial documents like checks or credit card numbers.
You don’t want your personal financial information stolen by anyone, so before using any banking app, check it out thoroughly first by visiting the developer’s website.
Malware and Antivirus Software
Most people think of malware as a virus that can harm your computer. However, it’s also possible to get malware by clicking on a link in an email or a search engine.
Antivirus software is an essential part of cyber security. It checks for malware and blocks it before it infects your system. Most antivirus programs also have firewall features that help protect your PC from other types of threats like spam and phishing websites.
Some antivirus programs offer more features than others, so read the reviews before buying one.
Spam Filtering
Spam filtering is one of the most important aspects of maintaining your online security. Spam is any message that you do not want to receive. It can be anything from unsolicited advertisements to email messages that promote other websites or products.
The best way to prevent spam filters from blocking your legitimate email messages is by creating a list of trusted senders/receivers. Usually, you can do this through your email program or with a service such as SpamCop.
Once you have created a list of trusted senders and receivers, it’s time to set up spam filters to prevent unsolicited emails from getting through to you.
Stay Safe Now!
Just as there are several ways to keep your physical security in check, there are numerous things you can do to help secure your online presence. Some of these steps might be obvious, while others may seem esoteric—but they all play a vital role in protecting yourself and those who rely on you.
The post 10 Tips To Help Enhance Your Online Security appeared first on Chi Go Dec.
]]>